Hello, Marinade community! This time we’re coming to you with new research — we’re sure you’ll find it interesting!
Old Problems in a New Wrapper
We received reports from fellow validators: they were approached with offers to join a so-called “private mempool without sandwiches” with promises of “security and high yield.” This sounded too good to be true. Together with @w3e_uk, we decided to validate these claims using on-chain metrics.
Summary
We observed recurring sandwich attacks originating from a specific program:
Program ID: inf69quFVZyuHEsrUXq3APtYLr4iqsNiQdCh5ArGcUp
Within a single slot, the front → victim → back pattern is clearly visible, often with splitting (multiple buys/sells around the same victim).
Based on slot distribution, the contract appears to be sourcing flow via a private mempool connected to a subset of validators.
From our initial sample, a significant portion of these validators hold delegated stake from @MarinadeFinance, @jito_sol, and @edgevana.
What We Measured
We collected transactions from the identified program and analyzed the blocks (slots) where it appeared. For each such block we:
-
Reconstructed the transaction ordering
-
Identified front-run → victim → back-run frames on the same token within a single slot
-
Allowed for splitting: multiple entries before the victim and multiple exits after
For each sandwich event we recorded:
-
Transaction indices within the block (positions)
-
Signatures of front/victim/back transactions
-
Number of entries and exits executed by the attacker
On-Chain Evidence
The sandwich pattern (front → victim → back) is consistently present, frequently with splitting. The contract often fragments both the “entry” and “exit” into multiple smaller transactions within the same block. This technique:
-
Obfuscates traces for superficial detection systems
-
Creates a false sense of trust in the private mempool, since monitoring tools like sandwiched.me, @0xGhostLogs, and sandwich finder @0x7cf are not yet capable of reliably detecting such fragmented sandwiches
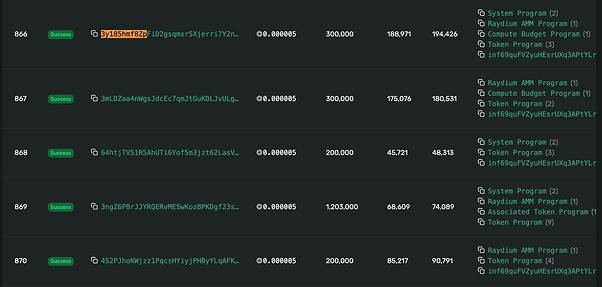
A clear example of a sandwich attack:
Buy 1:
3y185hmf8ZpFiD2gsqmxr5Xjerri7Y2noGdjBVPLZUdF5wsz7DyETjxZkXRryj9s56FZNwQCdLCuVw81y9DV89M1
Buy 2:
3mLDZaa4nWgsJdcEc7qmJtGuKDLJvULgMiMqQoAgCPx3Sj9THfPhzh4EKam7tTcTDyBxyGsmjqBufuqGarbGmXcQ
Transfer token to other wallet:
64htjTV51R5AhUTi6Yof5m3jzt62LasVzUFEkBXAb252d6teLwwQQe9rUVdXVFusr1vHEE8HR8gzbMGNJeKfzwAe
Victim:
3ngZ6P8rJJYRQERvMESwKozBPKDgf23sJiEDvvbZQxFyXQdnp7n5CZkY7vn6bswQib1wb9pdg8FcjtiX8S53B6dz
Sell all tokens:
4S2PJhoKWjzz1PqcsHYiyjPHByYLqAFK7TKAXkqFpXW56KicjWsfQX3PjJstw1Uvs4w8wwMAvByzv75udVJaDEam
Validators Processing Contract Flow
At the link below we provide a list of validator identity keys whose blocks contained transactions from the program (based on our dataset). For transparency, we include their activated stake (SOL) and tx_count (the number of times the program appeared in their slots within the analyzed range).
Conclusion:
Our sample shows significant delegations (including from Marinade, JITO, Edgevana, and others) to these validators. In practice, however, their blocks consistently carry traffic from a program exhibiting clear sandwich-bot behavior. This directly contradicts the claims of a “private channel without sandwiches.”
We will continue monitoring and publish further updates.
We hope the Marinade team and the teams behind sandwich attack analysis services will take note of this new sandwiching technique and promptly adjust their detection algorithms accordingly.